OpenVPN
Introduction
VPN
A virtual private network (VPN) is a private network that connects remote (and often geographically separate) networks through primarily public communication infrastructures such as the Internet. VPNs provide security through tunnelling protocols and security procedures such as encryption. For example, a VPN could be used to securely connect the branch offices of an organisation to a head office network through the public Internet.
There are two main types of VPN: remote-access VPNs and Site-to-site VPNs. Remote-access VPNs allow individual users to connect to a remote network such as roaming salespeople connecting to their company's Intranet. Site-to-site VPNs allow inter-connection of networks of multiple users for example, branch offices to the main company network.
OpenVPN
OpenVPN is a full-featured open source SSL VPN solution that accommodates a wide range of configurations, including remote access, site-to-site VPNs, Wi-Fi security, and enterprise-scale remote access solutions with load balancing, fail-over, and fine-grained access-controls. Starting with the fundamental premise that complexity is the enemy of security.
Requirements
Router Requirements
You will need an atheros ar71xx based router with at least 8MB of flash and 32MB of memory (e.g. TP-Link 1043ND, Netgear WNDR3700v1-2/3800, Buffalo WZR-HP-G300NH etc.), for this feature to work.
Connection Types
Remote-Access
Site-to-Site
Setup
In your router configuration select OpenVPN Configuration
–» Connection –» OpenVPN –» OpenVPN Configuration
- OpenVPN disabled
- OpenVPN Client
- OpenVPN Server
select option 1. - OpenVPN disabled
select option 2. - Setup router as a open VPN client
select option 3. - Setup router as a open VPN server
One very important caveat: If your router is configured as an OpenVPN client, per-IP bandwidth monitoring and per-IP quotas will not work. Quotas that apply to the whole network, and total bandwidth usage statistics will still be accurate.
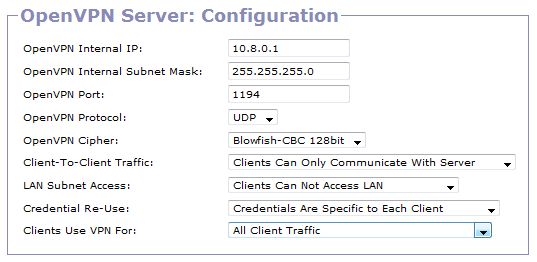
OpenVPN server
| OpenVPN Internal IP: | default = 10.8.0.1 |
| OpenVPN Internal Subnet Mask: | default = 255.255.255.0 |
| OpenVPN Port: | default = 1194 |
| OpenVPN Protocol: | default = UDP |
| OpenVPN Cipher: | default = Blowfish-CBC 128bit |
Client-To-Client Traffic:
- Clients Can Only Communicate With Server
- Allow Clients To Communicate With Each Other
select option 1. - All remotely connected clients to the openVPN server can only access the LAN
select option 2. - All remotely connected clients to the openVPN server can access the LAN and other remote clients.
When this option set to “Allow Clients”, each client will “see” the other clients which are currently connected. Otherwise, each client will only see the server. Don't use this option if you want to firewall tunnel traffic using custom, per-client rules.
LAN Subnet Access:
- Clients Can Not Access LAN
- Allow clients To Access Hosts on the LAN
Select option 1. - Remotely connected clients can not access the LAN.
Select option 2. - Allow remotely connected clients full access to the LAN.
Credential Re-Use:
- Credentials Are Specific To Each Client
- Credentials Can Be Used By Multiple Clients
Select option 1. - Client configuration file needs to made for each OpenVPN remote client
Select option 2. - Client configuration file can be used on more than one OpenVPN remote client
Clients Use VPN For:
- All Client Traffic
- Only Traffic Destined for Hosts Behind VPN
Select option 1. - If you on the road and you want all traffic (e.g. internet) to be routed through the openVPN server
Select option 2. - All traffic execpt Traffic Destined for Hosts Behind VPN to be routed through local connection
Note: If option 1. is selected Gargoyle controls all internet traffic for the connected client which could cause undesired and unexpected results.